Table of Contents
🚨 SECTION 1: THE BOARDROOM DISASTER
Imagine the boardroom.
A CISO presents their risk appetite statement: "We maintain a low-to-moderate appetite for cyber risk across our operations."
A board member leans forward: "You keep saying we have a ‘moderate risk appetite.’ What does that actually mean in numbers? How much are we really putting at risk right now?"
Silence.
Then come the auditors. Especially the regulators. They don't ask polite questions—they grill you. "Show us how you determined this was acceptable risk. Walk us through your quantification methodology."
And that's when it unravels.
The finger-pointing starts, with IT blaming the business units and vice versa. Compliance says they warned everyone. Legal gets involved.
In the worst cases? Someone gets fired. In the absolute worst cases? You're explaining penalties and non-compliance findings to the very board that's questioning your competence.
Time bomb
THE UNCOMFORTABLE TRUTH
If your risk appetite statement is vague, it's not protecting you. It's a ticking time bomb.
Let's be honest! your risk appetite statement probably fits in one paragraph, uses words like "moderate" and "appropriate," and couldn't survive five minutes of questioning from a regulator who actually knows what they're looking for.
And increasingly, that's not just embarrassing. It's a compliance violation.
━━━━━━━━●━━━━━━━━━━━━
You're 15% through — Section 1 complete
⚠️ SECTION 2: VAGUE RISK APPETITE
Think about what a real risk appetite statement is supposed to do: It's a "No" machine.
It should automatically kill bad ideas. When someone from business wants to launch a new customer portal without proper authentication, your risk appetite statement should provide the exact dollar threshold that says, "Sorry, this creates $8M in exposure and we've capped that category at $2M."
Instead, most organizations treat risk appetite like a fortune cookie: inspiring, vague, and completely useless for making actual decisions.
And increasingly, that's not just embarrassing. It's a compliance violation.
THE CONSEQUENCES ARE GETTING REAL
Regulators globally are moving from "show me your policy" to "show me your math."
Regulatory Warning
The consequences are getting real:
MAS in Singapore: Pushing firms to define operational resilience and risk appetite in ways that link clearly to business impact and tolerances, not just “we follow industry standards."
HKMA in Hong Kong: Emphasizing recovery time and impact tolerances for critical services. If you can’t explain what “maximum tolerable disruption” means in business terms, you’re not ready for an exam.
RBI in India: Expecting board‑approved cyber policies with defined thresholds and metrics that can be challenged and audited, not vague comfort language.
DORA in Europe: Forcing financial entities to prove digital operational resilience with concrete metrics and testing including impact tolerances, scenario exercises, dependency mapping. “We’re doing our best” isn’t a control.
SEC in the US: Requiring public companies to disclose material cyber incidents within four business days. You can’t decide what “material” means after the breach; you need that threshold defined in advance in business terms.
From APRA in Australia to SAMA in Saudi Arabia, supervisors are all converging on the same expectation: clear risk appetite, clear tolerances, and evidence that decisions match what the board approved.
See the pattern? It doesn't matter where you operate. Everyone wants the math. Nobody cares about your "comfort with risk” anymore and especially if you’re regulated or run critical infrastructure.
📊 QUICK POLL
━━━━━━━━━━●━━━━━━━━━━
You're 30% through — Section 2 complete
💡 SECTION 3: WHAT “GOOD” LOOKS LIKE

Quantify Risk
What Quantified Risk Appetite Actually Looks Like?
Forget frameworks for a second. Here's what you need to be able to say to your board:
💰 THE MONEY SENTENCE
"Our identity and access controls are currently at Maturity Level 2.8 on a 0-5 scale. Our board-approved risk appetite requires Level 4.0. The gap represents $4.5M in potential loss exposure. Here's the investment needed to close it: $800K over two quarters." That's a sentence a Decision Maker/ CFO can fund. That's a sentence an auditor can validate. That's a sentence that keeps you employed.
Now, how do you get there? You need a framework that provides:
Tiering - Not everyone needs maximum security
Maturity scoring - Numbers instead of "compliant/non-compliant"
Evidence standards - Proof that controls actually work
For example I'll use is CRI (Cyber Risk Institute) Profile v2.1—a framework built by the financial sector (major global banks and regulators). They took NIST CSF 2.0 and condensed 2,500+ regulatory requirements into 318 measurable diagnostic statements with clear proof standards.
You don't need to use CRI. You can use NIST CSF 2.0 directly, ISO 27001, CIS Controls, HITRUST (healthcare), NERC-CIP (energy), or whatever your sector demands. The architecture is what matters—and that's what I'm showing you.
Here's how the approach works:
1. Impact Tiering: Not Everyone Needs Maximum Security
The genius move? It admits that not every organization needs the same level of security.
Tier 1 institution (a major global bank, a large hospital system) requires near-zero tolerance for failure. Their impact tier means they complete all 318 diagnostic statements.
Tier 4 institution (a regional bank, a small clinic) can manage risk more aggressively to preserve margin. They complete 208 statements—a 35% reduction in scope.
This isn't "security by company size." It's security by systemic criticality. And it gives you an honest answer to "How much security is enough?"
2. Maturity Levels: The Language Executives Actually Understand
Instead of binary "Yes/No" compliance checkboxes, it uses a 0-5 maturity scale:
Level 0: We're winging it
Level 2: We have a policy (that nobody reads)
Level 4: We have automated controls with continuous monitoring
Level 5: We're teaching other companies how to do this
Now when a CxO asks "Where are we?" you can say:
"Our identity and access controls are at Maturity 2.8. Our board-approved appetite demands Level 4.0. The gap represents $4.5 million in potential loss exposure. Here's the investment required to close it."
That's a conversation a CFO can actually have.
3. Evidence Packages: Proof or It Didn't Happen
The framework defines exactly what an auditor expects to see. If you can't produce the "Example of Effective Evidence," the control doesn't exist.
This kills the compliance theater where you claim to have MFA deployed but 40% of your users are exempt "for business reasons."
━━━━━━━━━━━━●━━━━━━━━
You're 45% through — halfway there!
Want More Like This?
Get weekly cyber risk frameworks delivered biweekly.
No fluff. Just actionable guidance.
[Email input] [SUBSCRIBE TO MAZEOPS INSIGHTS]
Next Publication: "Secure Access Service Edge (SASE)" - Disaster"
📅 SECTION 4: YOUR 90-DAY ROADMAP
Alright, enough theory. Here's how you actually do this.
📅 Phase 1: Reality Check (Days 1-30)
What you're doing: Determining your Impact Tier
You can't set appetite until you know your weight in the ecosystem. Ask:
How many customers/patients/constituents depend on your systems?
What happens to the broader economy if you go down for 48 hours?
Are you cross-border? Multi-jurisdictional?
A Tier 1 org (systemic risk) requires near-zero tolerance.
A Tier 4 org (local impact) can accept more risk to preserve margin.
Deliverable: One-page Impact Tier justification for your board
💵 Phase 2: Show Me the Money (Days 31-60)
Stop reporting "We have 47 high-severity vulnerabilities." Start reporting "Our failure to patch these 47 systems creates $10-25M in exposure."
Using your chosen framework's maturity model:
Current State: Where are you today? (Maturity 2.3 on Access Controls)
Target State: Where does your appetite demand you be? (Maturity 4.0)
The Gap: What's the financial exposure of staying at 2.3?
THE FORMULA
"Our legacy payment systems lack MFA enforcement. Current maturity: 2.1. Target: 4.0. Gap exposure: $10-25M in potential production downtime plus $5-8M in regulatory penalties."

Risk Exposure
Deliverable: Risk Exposure Scorecard (see template below)
✅ Phase 3: Make It Enforceable (Days 61-90)
What you're doing: Embedding accountability into daily operations
This is where most programs die. You have the numbers, you have the gaps, and then... nothing changes because there's no enforcement mechanism.
Here's the fix: Risk Acceptance Templates
When a business unit wants to bypass a control (and they will), make the Business Head—not the CISO—sign a document that says:
📋 RISK ACCEPTANCE FORM
Control Being Violated: MFA requirement for customer-facing applications
Quantified Exposure: $8-12M maximum probable loss (production downtime + breach notification costs + regulatory penalties)
Business Justification: Faster user onboarding increases Q4 conversions by estimated $2M
Accountability: I, [Business Unit Head], accept full personal and professional accountability for the $8-12M exposure created by this exception to our Board-approved risk appetite.
Expiration: This exception is valid for 90 days and requires Board renewal.
Signature: ________________
Date: ________________
Watch how fast that "business justification" changes when it's the Sales Director's name on the liability, not yours.
Deliverable: Risk Acceptance Policy + Template deployed to all business units
📊 SECOND POLL
Results visible after voting. The good news: The next sections solve all four.
━━━━━━━━━━━━━━●━━━━━━
You're 60% through — keep going!
📊 SECTION 5: THE BOARD SCORECARD
Here's what you bring to your next board meeting instead of a 47-slide deck:
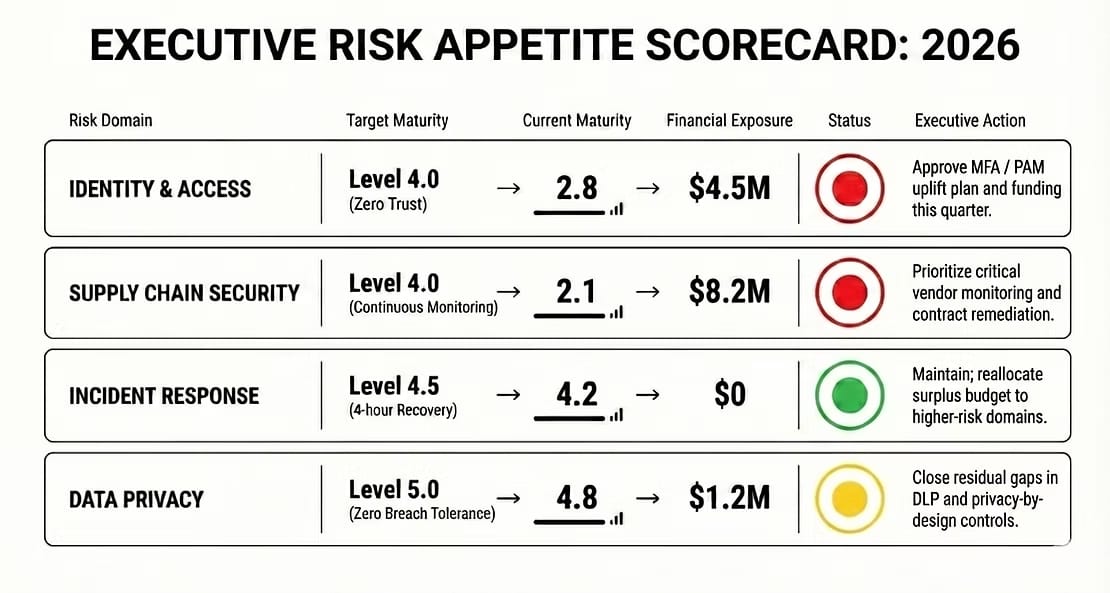
RISK APPETITE QUATERLY SCORECARD

Wining Strategy
STRATEGIC RECOMMENDATION
"We're reallocating $1.5M from Incident Response to address the Supply Chain gap, aligning with our appetite by Q3. An additional $2.8M is needed to close all red zones."
This is a table a board can understand. This is a table a CFO can fund.
━━━━━━━━━━━━━━━━●━━━━
You're 75% through — almost there!
⚖️SECTION 6: THE ACCOUNTABILITY SYSTEM
Let's be honest: The real reason risk appetite statements are vague is because specificity creates accountability.
If you say "We accept no more than $5M in aggregate cyber risk exposure," then when you're sitting at $12M, somebody has to explain why.
That's uncomfortable. It's supposed to be.
Here's how to make it work:
Quarterly Risk Appetite Reviews
Every 90 days, the CISO presents the scorecard above. For every domain in the red:
What created the exposure? (New project? Delayed remediation? Vendor change?)
Who accepted the risk? (Show the signed Risk Acceptance Form)
What's the plan to get back to green? (Timeline + budget required)
What gets cut if we don't get the budget? (Business impact of staying red)
This creates a forcing function. The board can't ignore red zones quarter after quarter without explicitly voting to increase risk appetite (which is a legally documented decision).
The Brutal Truth Nobody's Saying
Here's what I've learned after watching dozens of breach post-mortems:
THE FIRING PATTERN
The CISO almost never gets fired for the breach itself. They get fired for not being able to explain in dollars, with documentation why the breach was either:
1. Within acceptable risk tolerance, or
2. A risk they flagged, quantified, and were denied budget to fix

Fired
If you can show the board, "I told you on March 15th that we had an $18M exposure in supply chain security, here's the email, here's the risk acceptance form that procurement signed, and here's why we're now paying $22M in breach costs," you keep your job.
If you show up and say, "We have a low risk appetite and we got breached anyway," you're done.
━━━━━━━━━━━━━━━━━━●━
You're 90% through — finish strong!
🎯 SECTION 7: CHOOSE YOUR PATH
You have two paths from here:
Path 1: Keep the Vibe-Based System
Continue with "low risk appetite" statements. Hope for the best. When (not if) something goes wrong, scramble to explain to regulators, boards, and legal counsel why you couldn't answer basic questions like:
How much risk were you willing to accept?
How much risk were you actually carrying?
Who authorized the delta?
Path 2: Engineer Certainty
Spend 90 days building a quantified risk appetite statement using CRI Profile, NIST CSF, ISO 27001, or your sector-specific standard. Create the scorecard. Implement the risk acceptance process. Show your board that you're running security like a business function, not a prayer circle.
The regulators won't define the boundaries for you. Legal action won't be gentle. The time to choose is before the breach, not after.
Ready to Build Your Quantified Risk Appetite Framework?
Let's discuss your specific situation:
Connect on LinkedIn or email: [email protected]
What's driving this? (Board pressure? Audit finding? Upcoming regulatory exam? You're just tired of guessing?)
What's your biggest blocker? (Budget? Executive buy-in? Technical debt? All of the above?)
What does success look like in 6 months? (Be specific—not "better security" but "Board stops asking why we can't quantify risk")
I'll reply personally within 24 hours with specific guidance. Depending on where you are.
Get Weekly Frameworks Like This Join 500+ security leaders getting Mazeops Insight.
[Email Input Field] [SUBSCRIBE] Next Publication: "Secure Access Service Edge (SASE)" - Disaster"
Frequently Asked Questions
Q: What is a risk appetite statement?
A: A risk appetite statement defines how much cyber risk your
organization is willing to accept in pursuit of business objectives.
Q: Why do vague risk appetite statements fail audits?
A: They fail because they can't be measured, audited, or enforced.
"Moderate risk tolerance" provides no actionable guidance.
Q: How long does it take to create a quantified risk appetite statement?
A: Following our 90-day roadmap, you can build a board-ready,
dollar-quantified risk appetite statement in three months.
Q: What framework should I use?
A: Choose based on your sector: CRI Profile (finance), NIST CSF
(universal), ISO 27001 (global), HITRUST (healthcare), or NERC-CIP
(energy).
ONE LAST THING
If this resonated with you, forward it to your key decision maker, your General Counsel, or whoever keeps asking you "how much security is enough?"
The answer is no longer "it depends."
The answer is math.
Let's do the math together.
Access this article also on
mazeops:
━━━━━━━━━━━━━━━━━━━━
Section 7 complete — You made it! 🎉
